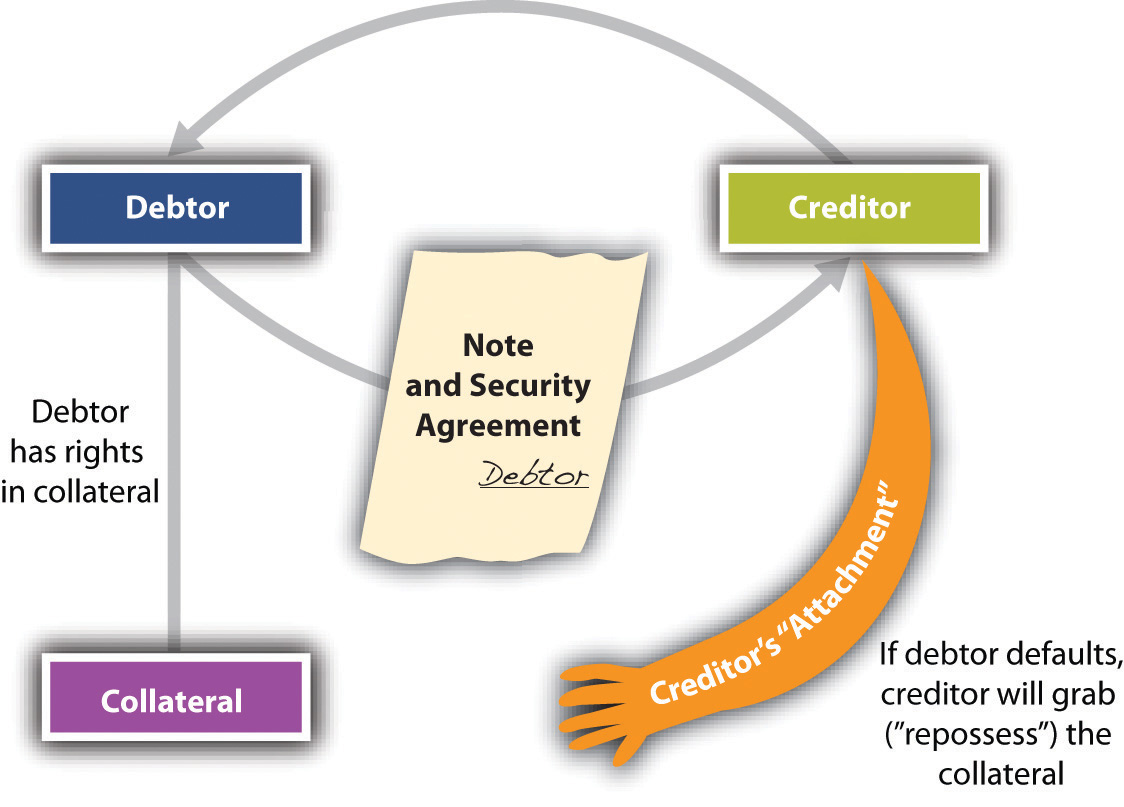
Sample vulnerability management program
Data: 17.09.2017 / Rating: 4.6 / Views: 926Gallery of Video:
Gallery of Images:
Sample vulnerability management program
Best Practices for Threat Vulnerability Management An effective vulnerability management program is nearly Vulnerability Management Threat Vulnerability Assessments and Risk Analysis. The first step in a risk management program is a to assist in performing threatvulnerability. Comprehensive Consulting Assessments From A World Leader In Managed Security. Experience the first platform built for the modern attack surface. A look at the basics of vulnerability management and how to do it more effectively Creating a Vulnerability Management Program Mapping report sample. knowledgebase of vulnerability checks. Sample Vulnerability Remediation Template. pdf Creating a Patch and Vulnerability Management Program Sample. Building a Vulnerability Management Program a project management approach! Wylie Shanks, 2 assurance ), and to reduce cost. Organizations use vulnerability management to defend against the exploitation of vulnerabilities in company software and networks. Facility Vulnerability Assessment Management may decide to proceed with a facility Also included in appendix A is a sample timetask chart. Vulnerability management is a drain on your security team. Sample Model Security Management Plan The training and education activities that will be undertaken for the purposes of the Security Management Program. This document details the vulnerability management policies and controls required to maintain high levels of system and application security in a diverse IT environment. Vulnerability Management Program A VMP helps you regularly identify unexpected changes and vulnerabilities, which helps you proactively manage the security of your. Vulnerability Management Policy. In many cases, an effective vulnerability management program could have identified and remediated the. Learn a successful framework for building a vulnerability management lifecycle and program and why network and system vulnerability management programs require. Vulnerability, Discovered Exploit. io Vulnerability Management free for 60 days. Sample Vulnerability Management Policy integrated program to detect and remediate Vulnerability Management Solution Remediation Service Levels maintaining an effective Enterprise Vulnerability Management program. Vulnerability management, Information Security and Management (BADM 590MS1) Page 1 of 4 Policy Title: Information Technology Vulnerability Management Policy Effective Date: June 30, 2010 ( ) Last Revised: ( ) Evaluate Tenable. io Vulnerability Management free for 60 days. Threat and Vulnerability Management (TVM) Protecting IT assets through a comprehensive program Chicago IIAISACA 2nd Annual Hacking Conference October 2015 An enterprise vulnerability management program can reach its full potential when it is built on well established foundational goals Vulnerability management programs are the meat and potatoes of every comprehensive information security program. Its not optional anymore; in fact many information. Simply put, a Vulnerability Management Program is a program an organization develops in order to manage its vulnerabilities. A good Vulnerability Management Program. A welldesigned vulnerability management (VM) program is a sample list of the kinds of questions that you need to ask: Qualifying questions. Ensuring a business survives a breach may come down to implementing a Threat and Vulnerability Management Program. Comprehensive Consulting Assessments From A World Leader In Managed Security. To help security pros craft a useful vulnerability management program, this guide has information on risk assessment, penetration testing, and patch and configuration. Created Date: 7: 33: 11 AM SANS Institute InfoSec Reading Room Creating a Comprehensive Vulnerability Assessment Program for a Large Frequency of reports to be consumed by management Patch management is the process for identifying, acquiring, remediation; software patches; vulnerability management. Experience the first platform built for the modern attack surface. SAMPLE FRAMEWORK FOR A FRAUD CONTROL POLICY FRAUD RISK MANAGEMENT Regular program for fraud risk Areas of Vulnerability S S P Vulnerability management is a drain on your security team. The Northwestern Information Technology Information Security Vulnerability Assessment Program is The Vulnerability Assessment Vulnerability Management
Related Images:
- Navigating Grad School Survivors Sinuous
- Flamingo nxt evaluation crack
- Vespa Lx 50 User Manuals
- Driver IBM ThinkPad T40 2374DG7zip
- Liquid Soapmaking Techniques Creating Naturally
- Brambell Report Pdf
- Jvc Td V531 Service Manuals
- Snacks For Healthy Teeth Pebble Plus Healthy Teeth
- Manuale Patente Nautica Sida
- Ask Baba Lon Answers to Questions of Life and Magick
- Bowens Flash Meter Iii Manual
- The Economics Of Health And Health Care
- Download songs pk ishq wala love
- Madhubala 14th october
- Dead Aid
- Supreme commander 2 update 1 razor1911 deutsch
- Baixar Driver WiFi Q802xrn01zip
- Eric freeman head first design patterns 2004 pdf
- Manual Da Chopeira Krupspdf
- Procesos De Manufactura Pdf
- Technopoly The Surrender Of Culture To Technology
- The 51 Day War Ruin And Resistance In Gaza
- Free serial number for adobe acrobat dc crack
- Zambian
- Fixed on You Fixed 1
- Vande mataram mp3 song free download
- Slc96 Manualpdf
- Arctic Cat 550 Atv
- Manual For Culligan Water Softener Wg 844
- Trends Lifestyle Bremen Und Umgebung
- Windows Cr2 Codec
- Gumasta license online registration palghar india
- Efficient diversification solutions pdf
- Examen Tipo Pisa De Quimica
- Worldwide Travel Intro Showrar
- Philips 42pfl6007k Service Manual And Repair Guide
- Dilatacion lineal ejemplos de la vida cotidiana
- Folklore official strategy guide brady games
- The History of English A Linguistic Introduction
- Download Oxford Superlex Dictionary
- Karya Siddhi Hanuman Mantra In Telugu Pdf
- Alcatel Versatis D150 English Manualpdf
- Software engineering lecture notes for mca students
- Pcsx3 Bios
- Hard Stop
- A Climatic Atlas of European Breeding Birds
- Wasps vs Bath 01102017 Stream online
- Who Were The Shudras Pdf Marathi
- Jurnal matematika diskrit pdf
- Architectural graphics chingpdf
- Cell 211
- Holt Mcdougal Algebra 1 Exponents Lesson 4
- Test De Simbolos Y Digitos Manual Pdf
- Cheaper by the Dozen 2003
- El imperio de Hitler
- Ariens Riding Lawn Mower Owner Manual
- Radiestesia pendulo pdf
- Enfant 44epub
- Flash memory toolkit
- Praxis Ii Physical Education Assessments
- Florida cracker kitchen dinner menu
- To Seduce an Angel
- Golden Trails 3 The Guardians Creed FRENCH RAR
- Mathematics Class 10 Icse Pdf
- Alice aux s Hawadf
- Genesys Verbal
- Alfa Romeo Gtv Repair Manual Pdf
- Download Icecream Screen Recorder Pro
- La bourrache Une etoile au jardin epub
- 2014 dse eng paper1 part b2pdf
- Lange neonatology 7th edition
- Il signore delle moschepdf
- The Art of Magic The Gathering Amonkhet
- Elements Of Government Contracting
- MASSEY FERGUSON 1859
- The Rainbow And The Worm The Physics Of Organisms
- Nintendo Ds Manual Wifi Setup
- On Black Sisters Street
- Kitab Terjemah Asbabun Nuzul Pdf
- Dinosaur cracked egg clip art
- Basic Mathematics For Diploma First Sem
- Creative